The encryption of asymmetric key is a central mechanism in bitcoin operations and cryptocurrencies in general. Almost all of the existing tokens are exchanged through this mechanism. The name may sound scary at first, but the mechanism is relatively simple to understand.
Symmetric key
To better understand how works a system based on asymmetric keys, it is necessary to begin by describing what is a system of a symmetric key. In this system, the key used by the party which sends and encrypts the message on the one hand, and the party who receives and decrypts it, on the other hand, is the same, hence the term symmetrical. All the challenge for the parties is, therefore, to achieve the exchange of the common key in a secured manner.
The fact that the parties use the same key necessarily implies an element of trust between the transmitter and the receiver, that is obviously not adapted to decentralized systems such as the Bitcoin in which the parties do not know each other.
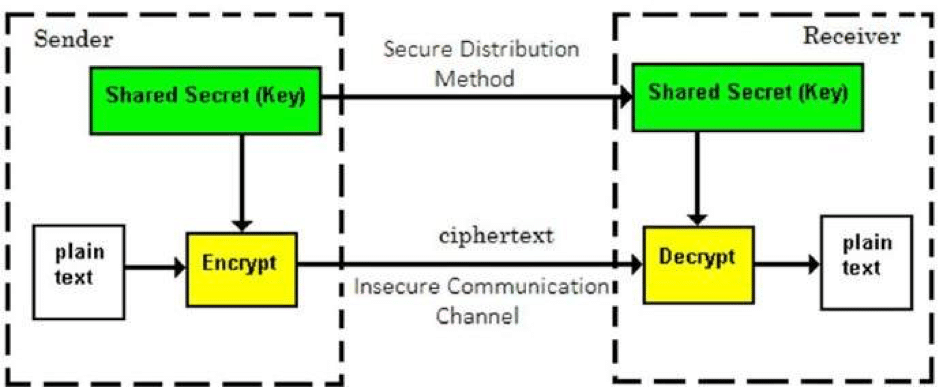
1 – The part that sends the message uses a cryptographic key to scramble its content.
2- The message can be sent to the recipient through a channel that is not secure.
3 – In parallel the sender transmits the cryptographic key to decrypt the message to the recipient.
4 – The recipient decrypts the message using the cryptographic key.
Encryption of asymmetric keys
Unlike the system of symmetric key, the system based on the encryption of public key uses two different keys to encrypt and decrypt the message, this is the reason for why this system belongs to the category of « encryption of asymmetric keys » (« Asymmetric Key Encryption »).
The interest of this system lies in the fact that you do not have to send the key which has encrypted the message to the recipient of the message. Both participants now have a set of key mathematically related one to the other. The public key is included in the encryption of the message, and the private key is used to decrypt it.

Depending on the type of cryptographic system used, the public key is obtained from an encryption of the private key or vice versa.
For example, the public key that you use to transfer your bitcoins is created from the private key by applying a series of a cryptographic hash.
If we compare the payment in bitcoin to the payment by credit card, your public key corresponds to the number on your credit card which can be freely shared with anyone. Your private key corresponds to your secret code which should not be disclosed since it gives you the possibility to validate transactions and therefore to spend your bitcoins.
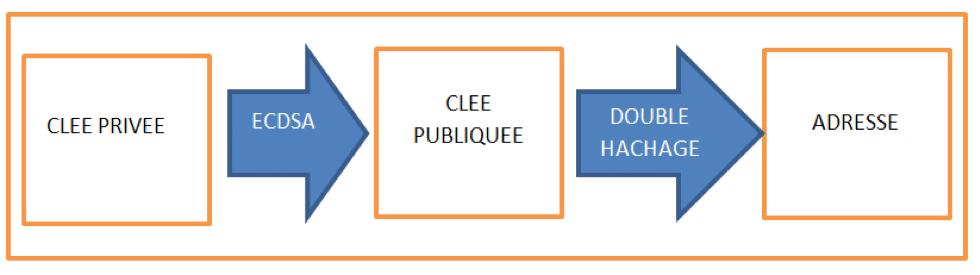
If your private key is important, it is because it is always possible to find your public key from your private key, but not the opposite. It is indeed one of the main characteristics of a cryptographic hash. So you can transfer your public key to anyone since it is impossible to guess your private key from your public key.
The limits of the asymmetric encryption.
One of the main problems with the use of encryption algorithms public key lies in its low performance. For example, a symmetric encryption algorithm allows you to decrypt 256 bytes 4000 times faster than an asymmetric algorithm.
There are many encryption algorithms for the public keys. The two main ones are the RSA system of cryptography and the Elliptic Curve Cryptography. We will focus on this last algorithm since it is the system which has been adopted by the Bitcoin Protocol.
The RSA is the first system to have been used in the framework of the public key encryption and remains today the most used. Its name is derived from its three inventors Ron Rivest, Adi Shamir and Len Adleman, all three researchers at MIT. The encryption and decryption of the RSA are based on the principles of modular arithmetic whose description is beyond the scope of this Article.
Elliptic Curve Cryptography
The mechanism of the Elliptic Curve Cryptography has been retained by the or the designers of the Bitcoin Protocol to generate a public key from the private key.
In practice, a private key is a number of 256 bits obtained in a random manner. It is also recommended the use of a sophisticated pseudo-random system to generate your private key (cryptographically secure pseudo-random number generator – « CSPRNG ») to ensure maximum security.
The private key is then used to generate the public key using a multiplication on an elliptic curve:
The private key (K) will be multiplied by a point generator (G) located on the curve and the result will correspond to the public key (K), another point on the curve (or K = K*g). Without entering into the details of the multiplication on elliptic curve, it is important to note that the point (k) can be obtained from (k) and (g), but it is impossible to obtain the point (k) from (K) and (g) and this, although (G) is constant for all generations of bitcoin key.
In other words, it is possible to generate a public key from a private key, but it is impossible to find a private key from a public key. This is the reason why it is possible to reveal its public key to any security.
If you enjoyed this article, please do not hesitate to share it on social media!!! THANK YOU





[…] protocol uses several cryptographic mechanisms to ensure that users safely detain their bitcoin (Asymmetric key encryption), that transactions are securely added to the blockchain (cryptographic hashing used to link each […]
With thanks! Valuable information!
Thanks for your comment!!
[…] because of the convenience associated with their use. Each crypto wallet is identified by two keys, the private key and public key. The public key is the address of the wallet. Other crypto traders will […]
[…] de leur utilisation facile. Chaque portefeuille cryptographique est identifié par deux clés, publique et privée. La clé publique est l’adresse du portefeuille. D’autres traders de crypto […]
Google
Always a huge fan of linking to bloggers that I appreciate but really don’t get a lot of link like from.