Internet of things is already a reality. You have of course heard about connected objects that are invading every day a little more our life. These are all the sensors installed in our cars, our houses, our smartphones, our towns…everywhere. And this is just the beginning.
For instance, several new hardware have recently appeared in our homes: Smart thermostats that regulate the temperature in accordance with our habits and weather data collected on the net, smart lights that ignite only when someone is in the room, the fridge that make orders online what is missing and get them delivered, or the Smart locks that close your house automatically, are all sensors that are now part of our environment.
These sensors are called intelligent because they are equipped with processors powerful enough to activate an algorithm able to learn our habits and combine them with information available on the net in order to update its setting accordingly.
Smart thermostats for instance, record the setting we are manually doing during the first two weeks and use weather forecasts available online to optimize energy savings. These devices can obviously interact with the other sensors of their environment. You can for instance program a smart thermostat to start increase the temperature of your home and turn the light on when your smart lock is opening the door. You can even do that when you are on your way home through your localization app on your smartphone.
We are just at the beginning of a new industrial revolution and Gartner, the famous IT and technology research company, estimates that the number of these connected objects might reach 13.5 billion in 2020. But this revolution raises many questions and especially security ones.

As shown during the attack organized in October 2016 against Internet Service Provider company Dyn, it is now possible to take control of thousands of connected objects such as webcams, routers, and even baby phones, to support a large scale DDos attack.
All these objects are organized in networks, so they will communicate with each other and realize transactions, billions of micro-transactions to be accurate. So it is paramount for all these transactions and communication to be conducted securely. These sensors are still not very smart, i.e their memory and processing capacity are still limited by the requirements of size and access to energy in their environments. Even if according to Moor’s Law, this situation will evolve sharply, it is necessary to find today a system able to secure these networks while understanding the requirements of the Internet of Things.
BLOCKCHAIN
A system based on the blockchain could appear at first sight as a good solution. A blockchain indeed allows a network of nodes or connected objects to communicate and transact in a secured and decentralized way.
However, in its current state of development, the bitcoin blockchain (that we are taking as an example here) has several inconvenient to be applicable to an important number of connected objects:
- not good for Scaling:
Due to the limited number of transactions that can be added to the blockchain, it is actually difficult apply the blockchain to a network with an exponential increase where transactions made among members of the network (either physical persons or not) will also increase exponentially. The size of each blockchain blocks is 1MB and even an increase of this size through SEGWIT 2X for instance, is not sufficient to process all the transactions made on the bitcoin network. It is indeed considered that 250,000 transactions are always waiting to be processed.
- A protocol very slow
This bottleneck is largely due to the speed of the bitcoin protocol which programmed to only add a block every 10 minutes. The difficulty of Proof of Work is indeed always adjusted to the number of miners acting on the network (i.e the amount of hashing power used on the network) so the time frame between two block will always be 10 minutes. It is easy to understand that such system which is already difficult to apply to commercial solutions, is not adapted to a universe where billions of machines exchanges with each other.
- high Fees
The presence of minors that must be paid for their validation work and adding blocks to the blockchain, is also a big disadvantage. At the present time, the fees charged by minors to users for each transactions added to the blockchain are around $2, but can reach of the peaks of up to 8.5 dollars. Here again the principle of the mining which aims to operate the network in a decentralized and secure manner, is particularly unsuited to micro-transactions that will explode around us in the near future.
- Heavy weight of the blockchain
Finally the size of the blockchain may also prove to be a major disadvantage. Even if it is not necessary to download a blockchain integrally to interact with it and send transactions, it still needs to be stored in a same place by all members (minors or nodes) of the network. This system is obviously unsuited to a world where billions of transactions will be carried out each day.
A POSSIBLE SOLUTIONS: THE LIGHTNING NETWORK

The Lightning Network is a protocol designed with the initial objective to enable the bitcoin to extend its network by accelerating the speed of the transactions.
This Protocol now applies to the whole of the blockchains and allows millions of transactions per second, instantly and with fees extremely low.
The technology used by the lighting network is that of channels of payments. The micropayments Channels are a technology that allows you to group several small transactions in a same transaction in order to limit the costs and not have to wait for the confirmation for each transaction.
Each party must therefore first create together a channel by issuing a transaction that they must all sign using their private key, which will not be broadcasted on the network and will block a certain sum of money.
The Lightning Network goes further and proposes a bidirectional channel, that is to say that the two parties can make payments through the same channel. The two parties may therefore block a sum of money in the mulit-sig initial transaction and perform transactions through this channel.
The Lightning Network goes further and proposes a bidirectional channel, that is to say that the two parties can make payments through the same channel. The two parties may therefore block a sum of money in the mulit-sig initial transaction and perform transactions through this channel.
The Lightning Network also organizes the networking of these different channels so as to enable the achievement of payments by interposed persons. To do this, the software will perform a series of steps that will allow Alice to transfer funds to Carol by the intermediary of Bob.
These steps are the following:
1- Alice requests Carol to create a value (for example a mixture of digit and letters), and to transfer to her the hash of this value as well as its address bitcoin.
2- Alice transmits the hash to Bob and tell him that she would send him a bitcoin if he shows the value that it has received from Carol proving that it has transmitted a bitcoin to Carol.
3- Bob receives the value (which checks the hash) on the part of Carol and transmits her a bitcoin in return.
4- Bob passes the value that it has received from Carol to Alice thus proving that it has transferred the bitcoin to Carol. Alice can therefore send him to turn a bitcoin safely.

As we can see, Alice uses the channel that Bob has put in place with Carol to transfer a bitcoin to the latter without knowing her. Obviously this scenario works with several intermediaries.
But as you may be wondering, what would happen if Alice changed her mind and decided no longer to transfer the bitcoin once she has received the value from Bob and that the latter has forwarded the bitcoin to Carol (step 4 above)?
This is where Hash Time-Locked contract come into action.
The lightning network uses a process called « Hash Time-Locked Contract » which includes both a timer ( » Time-Locked ») and a secret ( » hash »). If we take the example above of a transfer of bitcoin from Alice to Carol (directly, without including Bob to facilitate the explanation), the establishment of a Hash Time-Locked Contract is done according to the following steps:
1- Alice sends the bitcoin that she wants to transfer to Carol, toward a third-party address which requires the signature of both parties to be used (multisig address).
2- Bob can recover funds by sending them to an address that he controls at any time by adding its signature and the value that has been transmitted by Alice.
3- Alice can also send the funds to an address that it controls but only after a certain period ( » Time-Lock »).
This mechanism is then used at the level of the network. So Alice and Bob have also put in place a hash Time-Locked Contract. In our example above, Bob receives the value of Alice before transferring the bitcoin. The two channels are linked so if Alice does not want to transfer the bitcoin, Bob will be able to insert the value that it has received from Carol in the Hash Time-Locked contract in place with Alice and thus be certain to recover it.
As you can see the lightning network represents a significant advance in the development of the bitcoin network and can be a solution for networks of communication between machines that are currently developing. Although many of the prototypes of networks based on a blockchain are currently in development, we would like to stop on one of the most promising, in any case the Internet of Objects, the Tangle.
TANGLE : all the advantages of the blockchain, without the blockchain.

Used by the IOTA project, Tangle is a new type of network based on a DAG (Directed Acyclic Graph) which has been designed with the Internet of Things in mind.
Tangle is no longer really a blockchain properly speaking, since there is no longer a « block » or a « chain ». Tangle is actually a second generation blockchain that does not rely on an architecture of blocks connected to each other by cryptographic hashes, but retains some of the fundamentals of the current blockchain:
– A peer-to-peer network
– A decentralized database
– A consensus mechanism to validate transactions
One of the first consequences of the absence of blocks is the absence of minors. To be precise and as we shall see, there are no members of the network who are exclusively minors on behalf of the network. All members are a little bit. A network based on Tangle does not charge fees to validate transactions. This is one of the major differences with the blockchain as we know it today. Transactions even for small amounts are therefore possible on this type of network, which is particularly well suited to the Internet of objects.
An improved consensus system applied to a revolutionary structure
The consensus mode is also different from the one we currently know since it is not done in sequence, 10 minutes for the bitcoin protocol for example, but continuously and in parallel.
TANGLE is also called a DAG or DIRECTED ACYCLIC GRAPH. « Directed » means that it only goes in a sense, « Acyclic » means that it is not circular and « Graph » that the network itself is the equivalent of the blockchain to store transactions.
As with current networks, each network member (or « node ») is a computer that sends transactions for validation to other members with whom it is connected. In the case of Tangle, these transactions are referred to as « Site ».

The rule is that any new transaction, called « tips » (in gray above), must approve two existing transactions. Each chain of transactions is called a branch. The longer the branch on which a transaction is based, that is to say there is more new transactions after it, the more its weight is important. By « weight », it is necessary to understand the amount of work that has been invested in the transaction by the Member transmitter. The weight of a « tip » can also be calculated in accordance with the weight of all transactions that are included on the same branch.
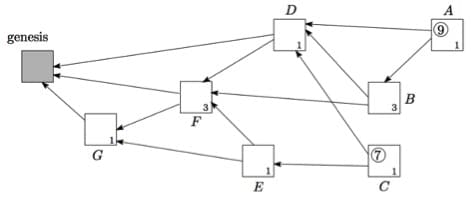
We then speak of accumulated weight. In the example above, the accumulated weight of A is 9, that is to say its weight (1), plus the weight of the transactions to which it points, or (b), (d), (f) and (G). The greater the weight of a site, the lesser it will be possible to revert on this transaction. It is important to see that all transactions in green in the above diagram are indirectly pointed by all new transactions in grey, which is not the case of the transactions in red. The objective of any transaction is to become green.
The two transactions that must validate each new transaction are randomly selected by an algorithm called « Markov chain Monte Carlo » and intends to avoid that Members choose to validate only their transactions. As you can see, each member of the network plays the role of a minor by validating two transactions for the Siena is accepted by the network.
How do you know the degree of reliability of a transaction?
By simply activating the algorithm « Markov chain Monte Carlo » to determine the number of times that a Tip chooses led to your transaction. If you activate the algorithm 100 times and that your transaction is reached 50 times then the rate of validation is of 50%.
Once a member has verified that the two transactions selected by the algorithm are not conflicting, the principle used to validate transactions is the same as that used by the blockchain of bitcoin, i.e. proof of work. Each Member reproduced the same cryptographic hash until it discovers the Nonce which allows you to validate the transaction. The big difference with the POW used for the bitcoin lies in the fact that there is no race between the different minors anymore and therefore the difficulty to find the Nonce does not increase. It is therefore possible to participate in the mining of the transactions of a network based on the tangle technology from its smartphone or its PC. Tangle is in fact designed so that the mining is done by objects connected with low capacities. It is therefore perfectly adapted to the Internet of Objects.
SCALING
It is essential to understand that the type of mining that we have just described is carried out simultaneously by all the members of the network and not more in cadence, all 10 minutes as is the case with the bitcoin. Therefore the more Members present on the network, the more secure the network is. This option is made possible because the transactions are no longer added to blocks whose size is limited, but are saved directly in the DAG or directed acyclic graph.
OFFLINE
Another crucial element for its use in the Internet of objects is that the members of the network can participate in the mining without being continuously connected to the Internet network. When we apprehend the issues of communication of the sensors to a network in the real world, it is apparent that this option is indispensable. For practical reasons, it is in fact impossible that all connected objects are permanently connected to the Internet, even indirectly through a gateway.
I hope this article was useful !! If so you can like the page. Please also do not hesitate to ask your question in the comments below !





I think this is among the most important info
for me. And i’m glad reading your article.
But want to remark on some general things, The web site style is ideal,
the articles is really great : D. Good job, cheers
Thank you for the feedback and support!
Google
We like to honor many other net internet sites on the internet, even though they arent linked to us, by linking to them. Underneath are some webpages worth checking out.
Google
Here is a superb Blog You might Discover Intriguing that we encourage you to visit.
Google
Every once in a although we choose blogs that we read. Listed below would be the most up-to-date web pages that we choose.