A hashING algorithm organizes the implementation of a hash function as a set of digital values.
This introduction may seem difficult to understand, yet the concept is not difficult to get. Of course we are not going to enter into the details of the functioning of the algorithm, but we will describe what it is to be used.
In the framework of the Decentralized Ledger Technologies (i.e blockchain technologies), the hash function (which is applied by the algorithm) has for main object to compare groups of important data and determine if their content has been corrupted or not. In fact, the hash of a group of data will always be the same as long as this group of data is not changed. By contrast, if a small change is made to this group of data, the hash of the new group will be totally different.
As its name indicates, a hashing algorithm cut the data to produce a new group of data completely different
Generally speaking, a hashing algorithm is a program to apply the hash function to « data of entries ». Concretely, a hash function is a mathematical function that allows you to convert a numeric value of a certain size in a numeric value of a different size. One could compare the hash function to a press in which is inserted an object, which once compressed exits with a smaller size, but always the same, regardless of the size of the inserted object.

In the above example, the hash algorithm is SHA256, which is the one used by the Protocol Bitcoin. The object to which is applies the function (« input ») is a numeric value whose size can vary according to the algorithm. Here the input are pieces of sentences, but it is possible to imagine any type of data (Figures, letters, signs…) having a different size.
The size corresponds to the number of characters which composed the group of data. The three inputs are therefore submitted together to the hash algorithm and the numerical value that results in (« output ») is however always of fixed size (between 160 and 512 bits according to the type of function). In the case of SHA256, the size of the output is always 256bits, or 256 characters…logic.
Hash functions propose many other features, that it is important to note:
- « Compression »: The input value (« input ») is generally greater than the value of output (« output »). In this case it is considered that the Hash Function compresses the data that are submitted to it.
- « Resistant to collisions »: two values of different inputs may not lead to a value of identical output. From this point of view the hash functions are Collision resistant. It should be noted that even a minimal variation between two values of inputs (a comma for instance) can lead to two values of outputs completely different.
The reverse is also true. The same value of entry may not lead to two different outputs. - « Pre-image resistance »: it is impossible to find an input value from the output. The only way to find the input value is to apply a method of « brute force », which means that the only way is to try all the input values possible until you find the good one. It is essential to understand this peculiarity in the framework of the crypto-currencies because the mode of consensus of the « Proof of the works » (« Proof of Work ») is based precisely on this concept.
A hash algorithm determines the way in which is going to be used the hash function. It is therefore important to differentiate between the algorithm and the function.
As mentioned, a hashing algorithm is a program to apply the hash function to an input, according to several successive sequences whose number may vary according to the algorithms. All of the sequences of hash form a series. During each steps of the series, two blocks of data whose size varies according to the algorithms (usually between 128-bit has 512-bit), are subject to the hash function with a view to obtain a « Output value » (« output »).
A frequency of the series of hash:
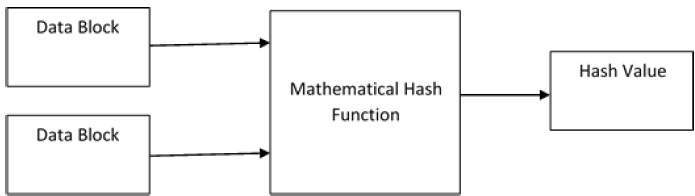
The output value is then one of the two blocks of data in the following sequence. The other block does generally constitute the data from the most recent block of data. This mechanism is repeated until the entire message has been submitted to the hash function. This is the reason for which it is often made reference to a « snowball effect ».
A hash serie:
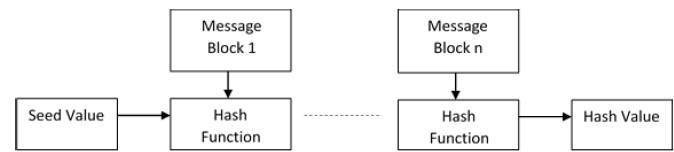
There are many types of hashing algorithm such as Message Digest (MD, MD2, MD4, MD5 and MD6), RIPEMD (RIPEND, RIPEMD-128, and RIPEMD-160), Whirlpool (Whirlpool-0, Whirlpool-T, and Whirlpool) or Secure Hash Function (SHA-0, SHA-1, SHA-2, and SHA-3). In the universe of the cryptocurrencies, the most used hashing algorithms are SHA-256 and X11.
The algorithm SHA-256,
SHA-256 (« Secured Hash Algorithm 256″) is the algorithm which has been chosen by the designers of the Protocol Bitcoin. It is used during the creation of the public key from the private key, but also for the realization of the process of proof of work. This algorithm has been developed by the NSA ( » United States National Security Agency ») in 2001 and continues to be used by many financial institutions and governments for the encryption of their data.
The success of the bitcoin however, poses an important problem concerning the use of the algorithm SHA-256. As we have already seen, each new bitcoin created returns to the miner who has carried out and submitted to the network the « Proof of work » the first. However, the likelihood for a minor to provide the « Proof of work » in the first position is directly proportional to the capacity of calculation that it is able to deploy on the network, i.e the hashing power.
On the other hand, the Protocol Bitcoin has been programed to add a block to the blockchain all 8-10 minutes, no more but no less. The Protocol Bitcoin adjusts therefore automatically to the hashing power of miners on the network by increasing or decreasing the difficulty of the « Proof of work ».
The popularity of the bitcoin has led to a rapid increase in the number of miners, thus we have seen a real race to the equipment of minors whose capacity of calculation and so hashing power, have literally exploded in recent years.
In a few years, we moved form the first miners who in 2009 could mine bitcoins on their laptops (Central Processing Unit mining – the « CPU ») or by improving its capacity with a graphics card (Graphic Processing Unit mining – « GPU »), to mining farms only using « Application Specific Integrated Circuits (ASIC). The ASIC are integrated circuits with a single function (for example mine bitcoin) and not a general vocation. So ASIC can mine hundreds of thousands times more rapidly than the CPU and GPU, for a fraction of their energy consumption and thus the cost, while producing less heat and noise.
The investments in the ASICs have rapidly increased thereby excluding all individual miners. The only way today for individuals to compete with the mining farms is to be part Mining pools, i.e huge groups of individual miners. Yet these groups occasionally reach worrying sizes for the bitcoin network to the extent that certain are in a position to exceed the fateful limit of 51% of the hashing power (« Hashrate ») and are thus potentially able to take control of the network. In practice, if a member gather more hashing power than the rest of the network, it has the ability to come back unilaterally on the blocks already added to the blockchain (see « The attack of 51% »). This was the case of the GHash mining pool which exceeded the threshold of 51% beginning 2014.
This concentration of hashing power which ended up in a race for the equipment of miners is the main problem of the use of the algorithm SHA-256 (with the disastrous ecological effects it generates), since it threatens the philosophy of the bitcoin. This algorithm is indeed likely to question the decentralized aspect the bitcoin.

The Algorithm X11
it is in this context that appeared the Algorithm X11 at the end of 2014. This algorithm which has been designed for crypto-currencies, is still more secure than the algorithm SHA-256 and presents the advantage of not being able to be used by « Application Specific Integrated Circuits ». It is currently being used in several crypto-currencies, the most famous being DASHCOIN.
X11 organizes a chain of 11 different hash algorithms: Blake, BMW, groestl, JH, keccak, skein, Luffa, cubehash, shavite, SIMD, and echo. To fail, the whole 11 hashing algorithms must default simultaneously. It is estimated that the probability of such a situation is close to zero.
On the other hand, as we have seen above, the ASICs can only be programed for one function, i.e SHA-256. Yet an ASIC will cannot be programed to proceed with the hash of two (or more) different algorithms simultaneously. This is the reason why ASICs cannot be used to perform the Algorithm X11 since it included 11 different algorithms.
Thank you for having read this article. If it has pleased You DO NOT HESITATE TO THE Liker or has the share. Your comments and questions are also welcome!!





[…] If you want to learn more on this concept, you can make on our article cryptographic hash – The guide to understanding everything. […]